VMware Inc’s eighth annual Global Incident Response Threat Report warns internet users of impending threats from rising geopolitically-motivated cyberattacks and Cyber Extortion. The report also adds that 65% of cyberattack defenders have confirmed an increase in cyber threats in the aftermath of Russia’s invasion on Ukraine as deepfakes, API attacks and other cyber disruptions have challenged global-security teams.
“Cybercriminals are now incorporating deepfakes into their attack methods to evade security controls,” said Rick McElroy, principal cybersecurity strategist at VMware.
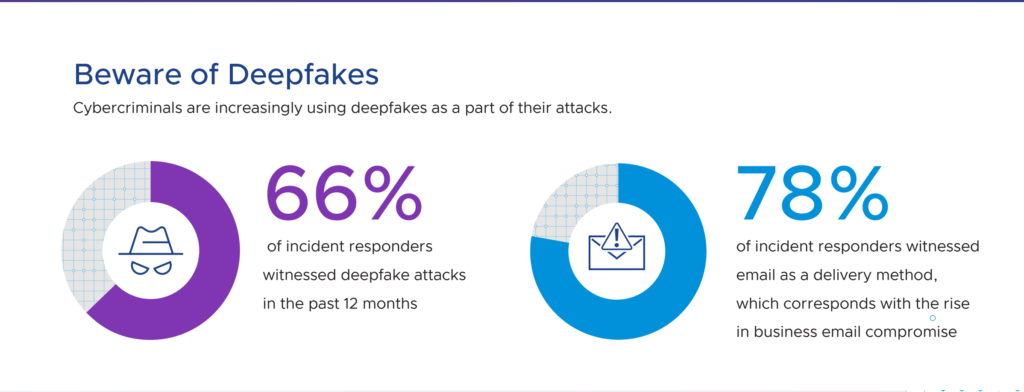
“Two out of three respondents in our report saw malicious deepfakes used as part of an attack, a 13% increase from last year, with email as the top delivery method. Cybercriminals have evolved beyond using synthetic video and audio simply for influence operations or disinformation campaigns. Their new goal is to use deepfake technology to compromise organizations and gain access to their environment.”
Additional key findings from the report include:
Cyber Pro Burnout
Forty-seven percent of incident responders said they experienced burnout or extreme stress in the past 12 months, down slightly from 51% last year. Of this group, 69% (versus 65% in 2021) of respondents have considered leaving their job as a result. Organizations are working to combat this, however, with more than two-thirds of respondents stating their workplaces have implemented wellness programs to address burnout.
Ransomware Actors Bring up New Cyber Extortion Strategies
The predominance of ransomware attacks, often enforced by e-crime groups’ collaborations on the dark web, has yet to let up. Fifty-seven percent of respondents have encountered such attacks in the past 12 months. Meanwhile, two-thirds (66%) have encountered affiliate programs and/or partnerships between ransomware groups as prominent cyber cartels continue to extort organizations through double extortion techniques, data auctions, and blackmail.
APIs as Next Target for Attackers
As workloads and applications proliferate,23% of attacks now compromise API security. The top types of API attacks include data exposure (encountered by 42% of respondents in the past year), SQL and API injection attacks (37% and 34%, respectively), and distributed Denial-of-Service attacks (33%).
Lateral Movement
Lateral movement was seen in 25% of all attacks. Cybercriminals leveraged everything from script hosts (49%) and file storage (46%) to PowerShell (45%) and business communications platforms (41%) and .NET (39%) to rummage around inside networks. An analysis of the telemetry within VMware Contexa, a full-fidelity threat intelligence cloud that’s built into VMware security products, discovered that in April and May of 2022 alone, nearly half of intrusions contained a lateral movement event.
“In order to defend against the broadening attack surface, security teams need an adequate level of visibility across workloads, devices, users and networks to detect, protect, and respond to cyberthreats,” said Chad Skipper, global security technologist at VMware.
“When security teams are making decisions based on incomplete and inaccurate data, it inhibits their ability to implement a granular security strategy, while their efforts to detect and stop lateral movement of attacks are stymied due to the limited context of their systems.”
Despite the turbulent threat landscape and rising threats detailed in the report, incident responders are reportedly fighting back. Incidentally, 87% say that they are able to disrupt a cyber-criminal’s activities sometimes (50%) or very often (37%). They’re also using new techniques to do so.
Three-quarters of respondents (75%) say they are now deploying virtual patching as an emergency mechanism. In every case, the more visibility defenders have across today’s widening attack surface, the better equipped they’ll be to weather the storm.
The report is based on VMware’s online survey about trends in the incident response landscape in June 2022. It is found that 125 cybersecurity and incident response professionals from around the world took part in the survey.The detailed report is available here: Global Incident Response Threat Report: Manipulating Reality.
VMware at Black Hat USA 2022
VMware will discuss the findings from this report and other key security topics in the sessions listed below. Check out VMware’s Black Hat booth #1620, and follow them on social @VMwareNews and in the VMware Newsroom.
Why Workloads Are More Secure on VMware Clouds
Wednesday, August 10 at 1:50 pm PT
Chad Skipper, Global Security Technologist
Stefano Ortolani, Threat Research Lead
Exposing Malware in a Linux-based Multi-Cloud Environment
On-demand
Dale McKay, Senior Technical Marketing Architect
Black Hat Interview with Tom Gillis
Black Hat Article by Giovanni Vigna and Stefano Ortolani
VMware Explore
In addition to VMware’s presence at Black Hat USA 2022, there will be more than 100 security talks at VMware Explore, the global multi-cloud industry event taking place August 29 – September 1, 2022 at Moscone Center in San Francisco. Register today to begin building your agenda.





