Cisco Talos is tracking a campaign targeting government personnel in India using themes and tactics similar to APT36 (aka Mythic Leopard and Transparent Tribe).
This campaign distributes malicious documents and archives to deliver the Netwire and Warzone (AveMaria) RATs.
The lures used in this campaign are predominantly themed around operational documents and guides such as those pertaining to the “Kavach” (hindi for “armor”) two-factor authentication (2FA) application operated by India’s National Informatics Centre (NIC).
This campaign utilises compromised websites and fake domains to host malicious payloads, another tactic similar to Transparent Tribe.
Bengaluru, NFAPost: Cisco Talos, one of the largest commercial threat intelligence teams in the world, has published its report “Operation Armor Piercer: Targeted attacks in the Indian subcontinent using commercial RATs” which states that government employees and military personnel in India are under cyber attack from outside the country.
The report found that a malicious campaign targeting government employees and military personnel in India with two commercial and commodity RAT families known as NetwireRAT (aka NetwireRC) and WarzoneRAT (aka Ave Maria).
According to the report, Armor Piercer distributes malicious documents to deliver Remote Access Trojans (RATs) and gain access to highly confidential information related to government and defence agencies. Armor piercer or mail piercer is one of the traditionally made Japanese swords (nihontō) that were worn by the samurai class.
The lures used in this campaign are predominantly around operational documents pertaining to “Kavach”, a two-factor authentication (2FA) app operated by India’s National Informatics Centre (NIC) and used by government employees to access their emails. It utilises compromised websites and fake domains to host malicious payloads, another tactic similar to Transparent Tribe.
The earliest instance of this campaign was observed in December 2020, utilising malicious MS Office documents, known as maldocs, disguised as security advisories, meeting schedules, software installation guides, etc.
Sophisticated threat
As with all advanced threats that are rapidly becoming more sophisticated, this campaign was found to be using multiple techniques and evolved to obfuscate itself and remain in the victim’s environment, evading standard detection techniques – it continues to operate even today.
Armour Piercer illustrates another instance of a highly motivated threat actor using a set of RAT families to infect their victims. These RATs are packed with many out-of-the-box features to gain complete control over the infected systems.
The use of RATs makes it challenging to track down the threat actors behind it. In addition, since July 2021, Talos researchers have observed the deployment of file enumerators alongside RATs, indicating that the attackers are expanding their arsenal to target their victims.
This is just one example of the rapidly expanding threat landscape that is simultaneously becoming far more complex. In response, every company across sectors is rethinking their cybersecurity posture.
Cybersecurity vulnerabilities
Commenting on how organisations can strengthen their threat detection and response, Cisco India and SAARC Security Business Director Vishak Raman said operation Armor Piercer is a grim reminder of the vulnerabilities still existing in cybersecurity posture.
“To ensure end-to-end security of India’s most precious assets and information, government and defence agencies must implement a layered defence strategy that enables comprehensive visibility and coverage across all endpoints, accelerates response by leveraging automation and orchestration to enrich data, and reduces massive data sets into actionable insights through AI/ML and data analytics. Essentially, security must not be bolted on, rather built into every system and process to ensure infallible protection of people and assets,” said Vishak Raman.
Apart from artifacts involved in the infection chains, the report also discovered the use of server-side scripts to carry out operational tasks such as sending out malicious emails and maintaining presence on compromised sites via web shells. This provides additional insight into the attacker’s operational TTPs.
HOW DID IT WORK?
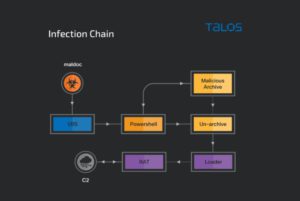
This campaign uses a few distinct, yet simple, infection chains. Most infections use a maldoc that downloads and instruments a loader. The loader is responsible for downloading or decrypting (if embedded) the final RAT payload and deploying it on the infected endpoint.
In some cases, the report observes the use of malicious archives containing a combination of maldocs, loaders and decoy images. The RAT payloads are relatively unmodified, with the command and control (C2) IPs and domains being the most pivotal configuration information.
INFECTION CHAINS
The earliest instance of this campaign was observed in December 2020 utilising malicious Microsoft Office documents (maldocs). These maldocs contain malicious VBA macros that download and execute the next stage of the infection — the malware loader.
The maldocs’ content ranges from security advisories, to meeting schedules, to software installation notes. These maldocs contain malicious macros that download and execute the next stage payload on the victim’s endpoint. The final payload is usually a RAT that can perform a multitude of malicious operations on the infected endpoint.
The maldocs pose as documents related to either meeting schedules pertinent to the victims, or as technical guides related to the Government of India’s IT infrastructure. It is likely that these files are either delivered as attachments or links in spear-phishing emails where the verbiage is meant to social engineer the victims into opening the maldoc attachments or downloading them from an attacker-controlled link.
Some file names used are:
KAVACH-INSTALLATION-VER-1.docm
Security-Updates.docm
Online meeting schedule for OPS.doc
schedule2021.docm
Toward the beginning of June 2021, the attackers started experimenting with the use of Pastebin as a payload-hosting platform. The downloader reached out to a Pastebin URL via cURL to download and inject the payload into its own running process.
Evolution of the downloaders:

Next Steps: Remediating ‘Armor Piercer’
This campaign has been ongoing since the end of 2020 and continues to operate today. Use of RATs makes it difficult to attribute and to track down threat actors behind it. Since July 2021, Talos researchers have observed deployment of file enumerators alongside RATs. This indicates that the attackers are expanding their arsenal to target their victims: defence and government personnel in India.
How to protect your organisation from such threat campaigns?
There is no ‘one solution’ to defend against modern cyber threats. Layered defence with the following characteristics helps to apply a highly effective cyber defence strategy.
Long Term Steps
1. Expand visibility – Comprehensive coverage across attack surface – Endpoint, Email, Web, Network, Cloud, Data & Apps is necessary
2. Reduce data – Apply AI/ML analytics to reduce massive data sets to actionable insights
3. Accelerate response – Utilise automation and orchestration to enrich data, apply context across threat defence tools, avoiding siloes.
Tactical Steps (Short Term)
1. Continuous monitoring using an EDR – Prevent, Detect and Respond to threats using suitable Endpoint Detection and Response tools. Utilise Managed EDR and Threat Hunting services to augment for skillset gaps inhouse. Choose to use automated actions to contain threats as and when discovered using relevant playbooks.
2. Email Security – Email is the no.1 threat vector to-date; an attack vector most threat campaigns use for spear-phishing its victims and to deliver malicious payloads. Utilise an email security solution agnostic to mail delivery solutions combined with advanced threat and phishing protection capabilities.
3. Use an Adaptive MFA to protect email accounts from account compromise/takeover. Extend this capability across enterprise to enable zero trust access control across organisations application footprint.
4. DNS & Web Security – All things on the Internet starts with Recursive DNS; The first layer of defence for cyber security attacks. Cascade DNS Security capability with Web Security to prevent access to CnC call-backs, Phishing and Malware domains, scanning for malicious downloads etc. Monitor shadow IT usage and scan for malware in clouds beyond on-prem DC.
5. Security Analytics and Network Detection & Response – Detect insider threats using ML-based behaviour anomaly detection tools. Identify and contain zero-day threats and malware in encrypted payloads missed by other layered defence tools
6. XDR – Too many alerts and alarms leads to alert fatigue. Choose a right XDR tool that integrates well with above security control points seamlessly, delivering visibility, threat investigation and automated response from a unified platform.





